Course Structure
Structure of the MOOC
This MOOC is organized into nine parts. Each part focuses on a particular topic in the area of Ethics and Cybersecurity. A preview of all videos is available at canvas-project.eu/results/mooc.html.
Sections 1–4: Fundamentals
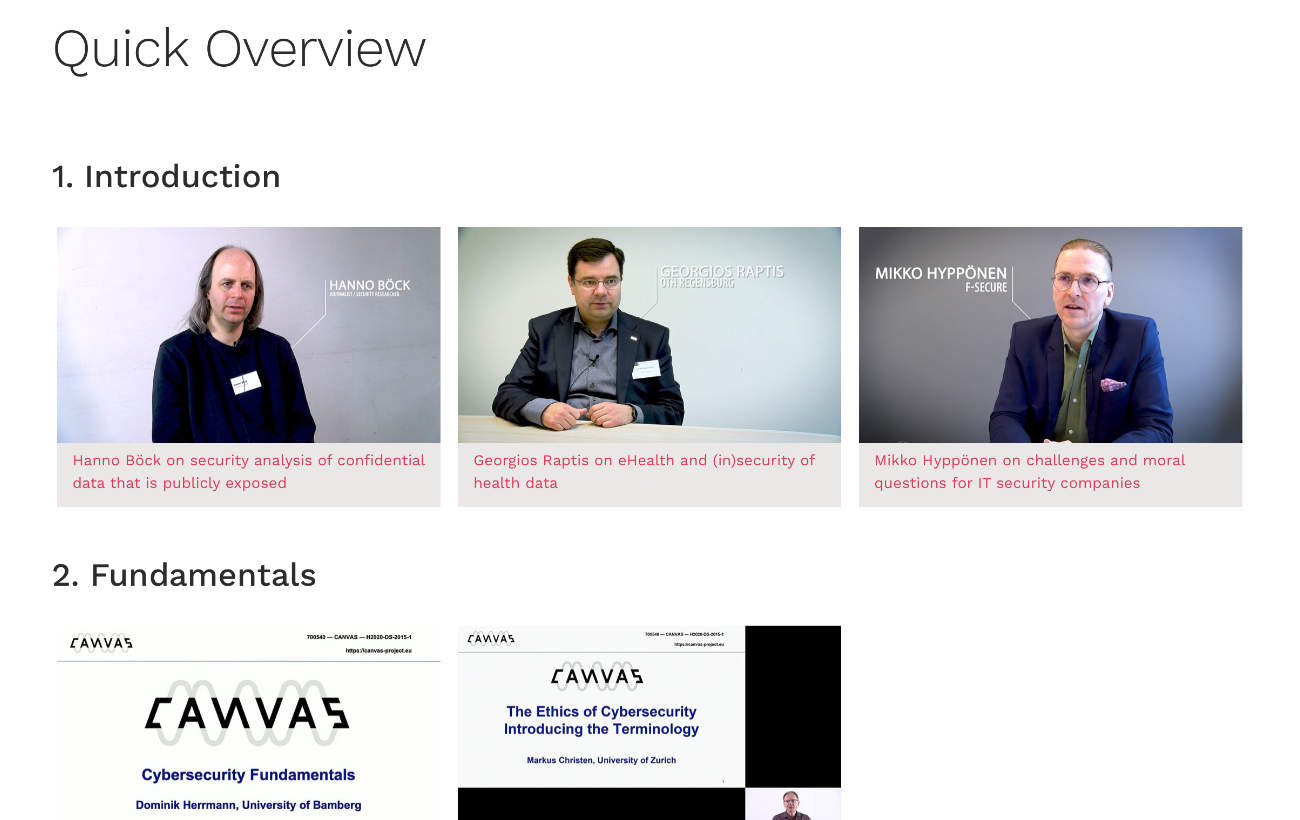
Part 1 introduces the problem landscape with three videos from information security practitioners.
Part 2 (Fundamentals) contains two introductory lectures on Cybersecurity and Ethics.
Part 3 (Applying Ethics to Cybersecurity) contains three introductory lectures. The first lecture demonstrates the challenges of applying frequently used frameworks to problems in cybersecurity. After that, you can apply the insights from this lecture to a contemporary dilemma (autonomous cars). The second lecture introduces the cybersecurity objectives within the European Union and how they relate to commonly shared values. The final lecture focuses on handling value conflicts. The part concludes with a short video in which a security researcher describes a particular value conflict.
Part 4 (Technical and Legal Aspects of Privacy) focuses on the value of privacy. This part consists of two introductory videos, three problem descriptions, and supplementary material. The first introductory lecture presents the basic principles of the European General Data Protection Regulation (GDPR). Another lecture explains how the requirements lied out in the GDPR can be implemented with technical and organizational privacy techniques. After the introductory videos, there are three short videos with problem descriptions in which privacy practitioners report dilemmas one may encounter in the field. The part concludes with supplementary materials: recordings of two talks held at a workshop at University of Bamberg in 2019.
Sections 5–9: Specific Areas
Part 5 (Business) presents challenges and solutions for businesses that must protect their infrastructure. The part starts with an introductory lecture on the relevant stakeholder values. After the lecture, there are three short videos in which practitioners narrate challenges related to handling security incidents. The section concludes with supplementary materials.
While Part 5 focuses on businesses as users of information security technologies, Part 6 (Vulnerability Discovery and Disclosure) considers information security providers: Four experts report on the unique challenges and dilemmas they face at work. Again, there are supplementary materials at the end of the part.
Part 7 (Healthcare) is concerned with the healthcare sector, where information security and privacy conflict with efficiency. The introductory lecture on ethical cybersecurity in healthcare is followed up by problem descriptions by four experts from the field. The part is concluded by supplementary materials.
Part 8 (Law Enforcement and National Security) focuses on nation-state issues. The first three videos discuss issues related to the fight against cybercrime. Two additional videos focus on cyber warfare. The supplementary materials section contains a recording of a talk on digital violence.
Part 9 (Cybersecurity and Democracy) concludes the MOOC. It contains a short lecture on online political disinformation, followed by two videos that raise awareness for the problems caused by two particular developments. Again, supplementary materials conclude the part.